Fork bomb
In
History
Around 1978, an early variant of a fork bomb called wabbit was reported to run on a
Implementation
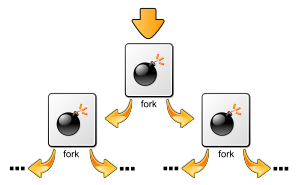
Fork bombs operate both by consuming CPU time in the process of forking, and by saturating the operating system's process table.[2][3] A basic implementation of a fork bomb is an infinite loop that repeatedly launches new copies of itself.
In
Microsoft Windows operating systems do not have an equivalent functionality to the Unix fork system call;[5] a fork bomb on such an operating system must therefore create a new process instead of forking from an existing one.
A classic example of a fork bomb is one written in Unix shell :(){ :|:& };:, possibly dating back to 1999,[6] which can be more easily understood as
fork() {
fork | fork &
}
fork
In it, a function is defined (fork()) as calling itself (fork), then
&).
The code using a colon : as the function name is not valid in a shell as defined by POSIX, which only permits alphanumeric characters and underscores in function names.
Prevention
As a fork bomb's mode of operation is entirely encapsulated by creating new processes, one way of preventing a fork bomb from severely affecting the entire system is to limit the maximum number of processes that a single user may own. On Linux, this can be achieved by using the ulimit utility; for example, the command ulimit -u 30 would limit the affected user to a maximum of thirty owned processes.[9]
On PAM-enabled systems, this limit can also be set in /etc/security/limits.conf,[10]
and on *BSD, the system administrator can put limits in /etc/login.conf.[11]
Modern Linux systems also allow finer-grained fork bomb prevention through cgroups and process number (PID) controllers.[12]
See also
References
- ^ a b Raymond, Eric S. (October 1, 2004). "wabbit". The Jargon Lexicon. Archived from the original on May 15, 2012. Retrieved October 15, 2013.
- ISBN 978-0470023242.
- ^ ISBN 978-1602670006.
- ISBN 0-07-061194-7.
- ISBN 1565926218.
- ^ Michal Zalewski (August 19, 1999). "[RHSA-1999:028-01] Buffer overflow in libtermcap tgetent()". Newsgroup: muc.lists.bugtraq. Retrieved December 10, 2022.
bash$ :(){ :|:&};:} - ^ "The Open Group Base Specifications Issue 7, 2018 edition IEEE Std 1003.1™-2017 Section 3.235". The Open Group/IEEE.
Name: In the shell command language, a word consisting solely of underscores, digits, and alphabetics from the portable character set. The first character of a name is not a digit.
- ^ "The GNU Bash Reference Manual, Section 3.3". Retrieved December 11, 2022.
When the shell is in POSIX mode (see Bash POSIX Mode), fname must be a valid shell name and may not be the same as one of the special builtins (see Special Builtins). In default mode, a function name can be any unquoted shell word that does not contain '$'.
- ISBN 1430319305.
- ISBN 978-0071767590.
- ISBN 978-1593271510.
- ^ "Process Number Controller in Documentation/ as appeared in Linux kernel 5.3". October 8, 2019. Archived from the original on October 8, 2019. Retrieved October 8, 2019.

