Network theory
| Part of a series on | ||||
| Network science | ||||
|---|---|---|---|---|
| Network types | ||||
|
||||
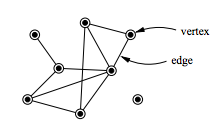
| Graphs | ||||
|
||||
| Models | ||||
|
||||
| ||||
In mathematics, computer science and network science, network theory is a part of graph theory. It defines networks as graphs where the nodes or edges possess attributes. Network theory analyses these networks over the symmetric relations or asymmetric relations between their (discrete) components.
Network theory has applications in many disciplines, including
Network optimization
Network problems that involve finding an optimal way of doing something are studied as
Network analysis
Electric network analysis
The analysis of electric power systems could be conducted using network theory from two main points of view:
- An abstract perspective (i.e., as a graph consists from nodes and edges), regardless of the electric power aspects (e.g., transmission line impedances). Most of these studies focus only on the abstract structure of the power grid using node degree distribution and betweenness distribution, which introduces substantial insight regarding the vulnerability assessment of the grid. Through these types of studies, the category of the grid structure could be identified from the complex network perspective (e.g., single-scale, scale-free). This classification might help the electric power system engineers in the planning stage or while upgrading the infrastructure (e.g., add a new transmission line) to maintain a proper redundancy level in the transmission system.[1]
- Weighted graphs that blend an abstract understanding of complex network theories and electric power systems properties.[2]
Social network analysis
Since the 1970s, the empirical study of networks has played a central role in social science, and many of the
Biological network analysis
With the recent explosion of publicly available high throughput biological data, the analysis of molecular networks has gained significant interest.[26] The type of analysis in this context is closely related to social network analysis, but often focusing on local patterns in the network. For example, network motifs are small subgraphs that are over-represented in the network. Similarly, activity motifs are patterns in the attributes of nodes and edges in the network that are over-represented given the network structure. Using networks to analyze patterns in biological systems, such as food-webs, allows us to visualize the nature and strength of interactions between species. The analysis of biological networks with respect to diseases has led to the development of the field of network medicine.[27] Recent examples of application of network theory in biology include applications to understanding the cell cycle[28] as well as a quantitative framework for developmental processes.[29]
Narrative network analysis
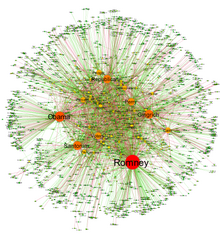
The automatic parsing of textual corpora has enabled the extraction of actors and their relational networks on a vast scale. The resulting narrative networks, which can contain thousands of nodes, are then analyzed by using tools from Network theory to identify the key actors, the key communities or parties, and general properties such as robustness or structural stability of the overall network, or centrality of certain nodes.[31] This automates the approach introduced by Quantitative Narrative Analysis,[32] whereby subject-verb-object triplets are identified with pairs of actors linked by an action, or pairs formed by actor-object.[30]
Link analysis
Web link analysis
Several
Centrality measures
Information about the relative importance of nodes and edges in a graph can be obtained through
Assortative and disassortative mixing
These concepts are used to characterize the linking preferences of hubs in a network. Hubs are nodes which have a large number of links. Some hubs tend to link to other hubs while others avoid connecting to hubs and prefer to connect to nodes with low connectivity. We say a hub is assortative when it tends to connect to other hubs. A disassortative hub avoids connecting to other hubs. If hubs have connections with the expected random probabilities, they are said to be neutral. There are three methods to quantify degree correlations.[37]
Recurrence networks
The recurrence matrix of a recurrence plot can be considered as the adjacency matrix of an undirected and unweighted network. This allows for the analysis of time series by network measures. Applications range from detection of regime changes over characterizing dynamics to synchronization analysis.[38][39][40]
Spatial networks
Many real networks are embedded in space. Examples include, transportation and other infrastructure networks, brain neural networks. Several models for spatial networks have been developed.[41]
Spread
Content in a
Network immunization
The question of how to immunize efficiently scale free networks which represent realistic networks such as the Internet and social networks has been studied extensively. One such strategy is to immunize the largest degree nodes, i.e., targeted (intentional) attacks[43] since for this case is relatively high and fewer nodes are needed to be immunized. However, in most realistic networks the global structure is not available and the largest degree nodes are unknown.
See also
- Complex network
- Congestion game
- Quantum complex network
- Dual-phase evolution
- Network partition
- Network science
- Network theory in risk assessment
- Network topology
- Network analyzer
- Seven Bridges of Königsberg
- Small-world networks
- Social network
- Scale-free networks
- Network dynamics
- Sequential dynamical systems
- Pathfinder networks
- Human disease network
- Biological network
- Network medicine
- Graph partition
References
- ^ PMID 24710095.
- ^ S2CID 44685630. Retrieved 2018-06-07.
- PMID 25115405.
- ^ Sindbæk S (2007). Networks and nodal points: the emergence of towns in early Viking Age Scandinavia - Antiquity 81(311). Cambridge University Press. pp. 119–132.
- .
- S2CID 228863564.
- S2CID 255247273.
- PMID 19372026.
- S2CID 144130904.
- PMID 36494627.
- ISBN 978-1-4051-0282-7.
- .
- PMID 28230844.
- ^ Alex Fornito. "An Introduction to Network Neuroscience: How to build, model, and analyse connectomes - 0800-10:00 | OHBM". pathlms.com. Retrieved 2020-03-11.
- PMID 33500525.
- . Retrieved 2014-10-15.
- MITPress, 2012.
- ^ Newman, M.E.J. Networks: An Introduction. Oxford University Press. 2010
- PMC 7123536.
- PMID 17222078.
- S2CID 158776581.
- .
- PMID 29795624.
- S2CID 143724478. Retrieved 22 September 2021.
- ^ Roberts N, Everton SF. "Strategies for Combating Dark Networks" (PDF). Journal of Social Structure. 12. Retrieved 22 September 2021.
- PMID 25290670.
- PMID 21164525.
- PMID 21865350.
- PMID 29021161.
- ^ a b Automated analysis of the US presidential elections using Big Data and network analysis; S Sudhahar, GA Veltri, N Cristianini; Big Data & Society 2 (1), 1–28, 2015
- ^ Network analysis of narrative content in large corpora; S Sudhahar, G De Fazio, R Franzosi, N Cristianini; Natural Language Engineering, 1–32, 2013
- ^ Quantitative Narrative Analysis; Roberto Franzosi; Emory University © 2010
- ISSN 0003-0007.
- S2CID 3032237.
- ^ Attardi G, Di Marco S, Salvi D (1998). "Categorization by Context" (PDF). Journal of Universal Computer Science. 4 (9): 719–736.
- S2CID 18365246.
- S2CID15186389.
- S2CID 7761398.
- S2CID 18979395.
- S2CID 119118006.
- doi:10.1109/49.12889.
- ^ Newman M, Barabási AL, Watts DJ, eds. (2006). The Structure and Dynamics of Networks. Princeton, N.J.: Princeton University Press.
- S2CID 2325768.
Books
- Dorogovtsev SN, Mendes JR (2003). Evolution of Networks: from biological networks to the Internet and WWW. Oxford University Press. ISBN 978-0-19-851590-6.
- Caldarelli G (2007). Scale-Free Networks. Oxford University Press. ISBN 978-0-19-921151-7.
- Barrat A, Barthelemy M, Vespignani A (2008). Dynamical Processes on Complex Networks. Cambridge University Press. ISBN 978-0-521-87950-7.
- Estrada E (2011). The Structure of Complex Networks: Theory and Applications. Oxford University Press. ISBN 978-0-199-59175-6.
- Soramaki K, Cook S (2016). Network Theory and Financial Risk. Risk Books. ISBN 978-1-78272-219-9.
- Latora V, Nicosia V, Russo G (2017). Complex Networks: Principles, Methods and Applications. Cambridge University Press. ISBN 978-1-107-10318-4.
External links

- netwiki Scientific wiki dedicated to network theory
- New Network Theory International Conference on 'New Network Theory'
- Network Workbench: A Large-Scale Network Analysis, Modeling and Visualization Toolkit
- Optimization of the Large Network doi:10.13140/RG.2.2.20183.06565/6
- Network analysis of computer networks
- Network analysis of organizational networks
- Network analysis of terrorist networks
- Network analysis of a disease outbreak
- Link Analysis: An Information Science Approach (book)
- Connected: The Power of Six Degrees (documentary)
- A short course on complex networks
- A course on complex network analysis by Albert-László Barabási
- The Journal of Network Theory in Finance
- Network theory in Operations Research from the Institute for Operations Research and the Management Sciences (INFORMS)